Azure Active Directory (AD) Groups have proven to be a silver bullet to control RBAC access, whether we talk about controlled access to resources or other Microsoft services using Office 365 groups and Security Groups. The idea of Azure AD Group is to minimize the manual permission assignment for any particular service or use case and rather have AD Groups as a member and manage the permission at the group level.
Let’s say if you have a dozen employees requesting access to any particular Azure service, say Analytics Resource Group, you’d want to create a Security Group, Analytics_Administrator with permission to Azure service, and then add all the employees to that Analytics_Administrator Group for permissions. This moves the permissions management to the group level and anybody who’s part of Analytics_Administrator will have the necessary permission automatically.
What’s New?
Microsoft has taken the Azure AD Groups to a next level and introduced the capability of doing the RBAC control for Azure AD Roles as you would do for any other resource access controls. With this feature, you can use AD groups to manage permissions for Azure AD Roles with minimum efforts. You no longer need to assign explicit AD Roles to any employee anymore and then keep a tab on ongoing changes.
Feature In-Depth
Create Group using Azure Portal
As you create a new security group in Azure, you’ll see an option ‘Azure AD roles can be assigned to the group‘ in GUI interface. As you turn this feature to ‘Yes‘, the created group can be used to control Role assignment to group level.
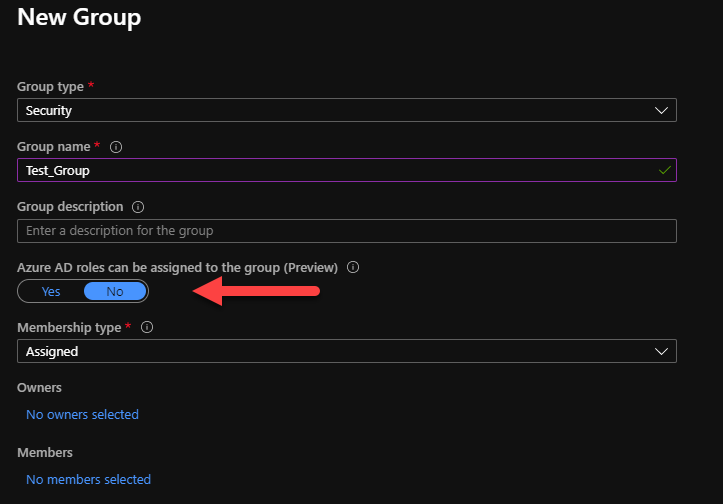
Create Group using Azure PowerShell
This feature can also be enabled using PowerShell or CLI deployment by setting isAssignableToRole to true, if doing programmatic deployments. You however can’t set this property on existing groups.
Install the Azure AD Preview module to get the up to date modules with new feature using the following command:
Install-Module azureadpreview
Import-Module azureadpreviewAs you install the preview module, use the following command to create a new group with role-assignable feature.
$group = New-AzureADMSGroup -DisplayName "GroupName" -Description "Group Description" -MailEnabled $true -SecurityEnabled $true -MailNickName "example" -IsAssignableToRole $trueWhile assigning the role permission to this newly created group, use the command New-AzureADMSRoleAssignment along with role definition and group ID.
Use the following command to get the desired role that you’d like to manage with this newly created group followed by another command to assign the role permission.
#Get Role Definition $roleDefinition = Get-AzureADMSRoleDefinition -Filter "displayName eq 'Security Administrator'" #Create a role assignment $roleAssignment = New-AzureADMSRoleAssignment -ResourceScope '/' -RoleDefinitionId $roleDefinition.Id -PrincipalId $group.Id
Limitations
With any new feature comes it’s own limitations. Since the feature is still in preview, there are some things to consider before you plan on adaptation.
- You cannot use the role-assignable groups with your custom AD roles.
- You cannot use on-premises groups to assign AD role permissions in Hybrid-AD scenario.
There are some ongoing known issue and changes being rolled out as the feature gets adopted more extensively. You can check the known issues at the link below:
License
There’s a minimum requirement of Azure AD P1 license to leverage this feature. If you are using Azure PIM, you must have Azure AD P2 to fulfill the license requirements.





